This enables merchants to accept card payments on smartphones and tablets, without the need to purchase a separate card reader. Instead, the merchant only needs to download a software application onto their mobile device.
This technology is a game-changer, especially for small and micro-merchants who are often slow to adopt new payments technologies, saving them the cost of purchasing devices whose sole purpose is to accept payments, and offering more robust security. As such, it is expected that PIN on Glass will encourage more merchants to accept cards and digital payments.
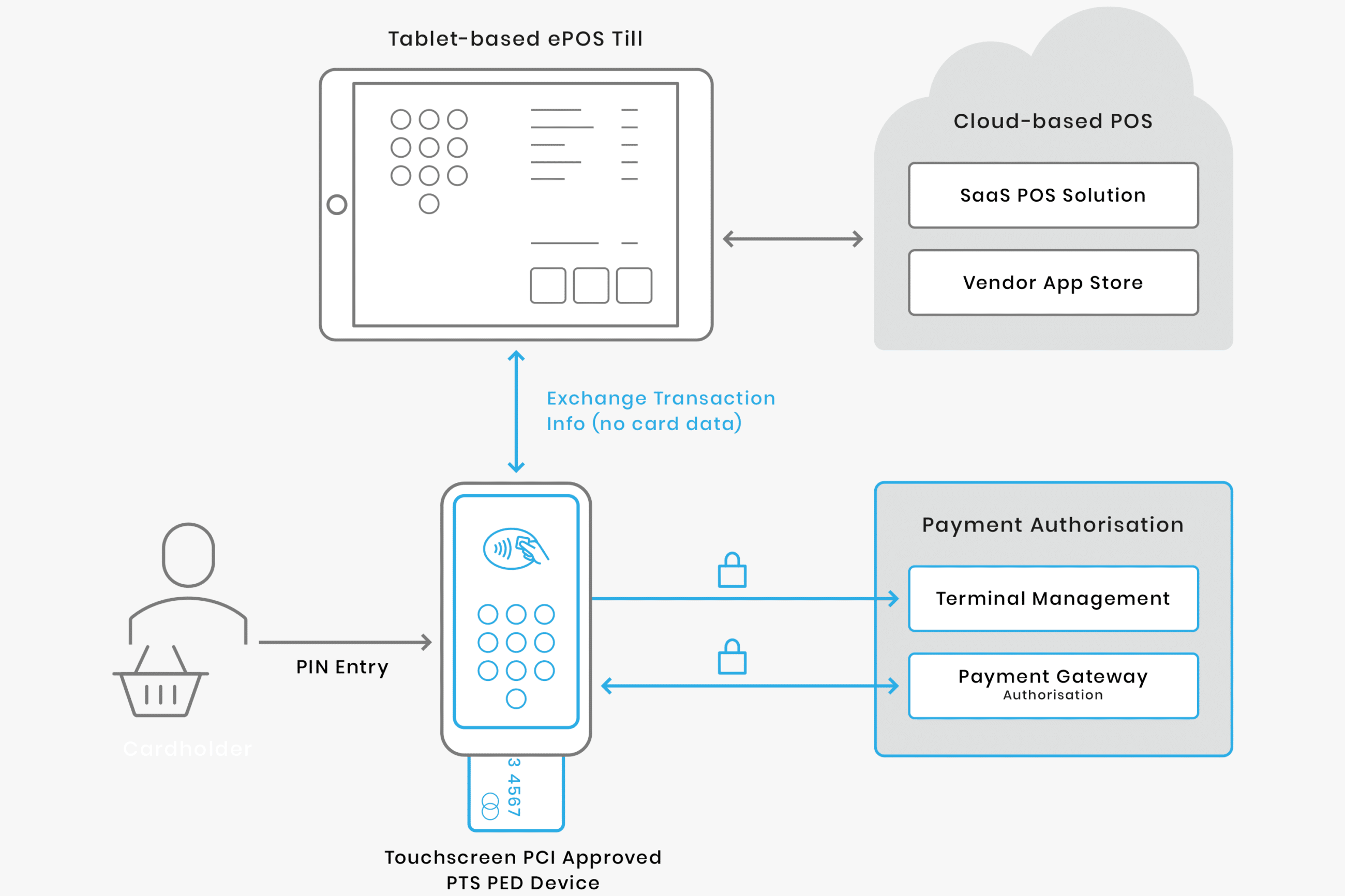
How does PIN on glass work?
There are 2 main types of PIN on Glass solutions:
- Approved Payment Card Industry PIN Transaction Device (PCI PTS) approved hardware-based point of interaction (POI) devices built on a mobile device platform and using the touch screen for PIN entry.
- Solutions meeting the PCI SSC’s Software-based PIN entry on Commercial Off The Shelf devices standard (SPoC on COTS solutions)
The first solution relies on hardware-based PIN entry and protection, through PCI PTS approval of specific mobile device platforms. The second solution offers software-based PIN entry and protection, on devices that meet the SPoC Standard, for use with any mobile device.
Although PIN on Glass is more secure than authentication methods involving a cardholder’s signature, software-based PIN entry introduces its own security vulnerabilities. COTS devices such as smartphones and tablets are designed to communicate with other devices, meaning they’re more vulnerable to interception. They were also never designed to accept payments.
The PCI standard seeks to address many of these issues using a few core principles. These include isolation of the PIN from the Primary Account Number (PAN) and other cardholder data, ensuring the security and integrity of the PIN entry software application, active monitoring of the software, and requiring a Secure Card Reader for PIN (SCRP) to encrypt and maintain the confidentiality of the account data. Furthermore, PIN on Glass transactions are restricted to EMV contact and contactless transactions.
Software-based solutions are not as secure as hardware-based solutions. Software-based solutions rely on software protection measures, such as white box cryptography and code obfuscation, to mitigate against attacks. However, given enough time, a determined attacker can break this security.
By comparison, hardware-based solutions involving a Trusted User Interface (TUI), provide a much higher level of security. Built into most modern smartphones is a hardware-isolated environment called a Trusted Execution Environment (TEE). For example, Trustonic’s TEE is integrated into 2 billion devices during manufacture. The TEE is designed to keep data and processes secure by separating them from the main operating system.
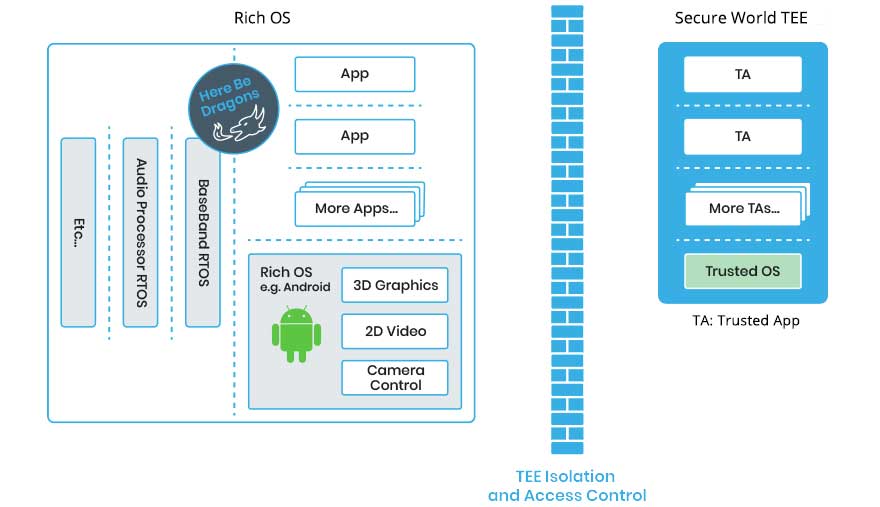
App developers can, as part of an app’s UX, temporarily take over the screen and touch sensors of a smart device at the hardware level, to provide a TUI. The TUI prevents malware attacking user interactions, such as PIN entry, because these interactions occur within the protected hardware environment of the TEE. This means that malware cannot capture the screen or simulate touches, even if the phone is rooted.
Up until now, the TUI has been difficult for app developers to use. The low-level APIs provided are extremely low level and so, in practice, the TUI was accessible only to a few expert developers, researchers and cybersecurity companies like Trustonic on the leading edge of new developments.
However, with Trustonic’s Application Security, this has all changed. TUI user interfaces can now be created easily using the new Layout Manager feature.
For more information about how to develop apps that use the TUI to protect the most critical, sensitive, and valuable interactions between users and their smartphone screens and keyboards, see our blog post on the benefits of a trusted user interface.

