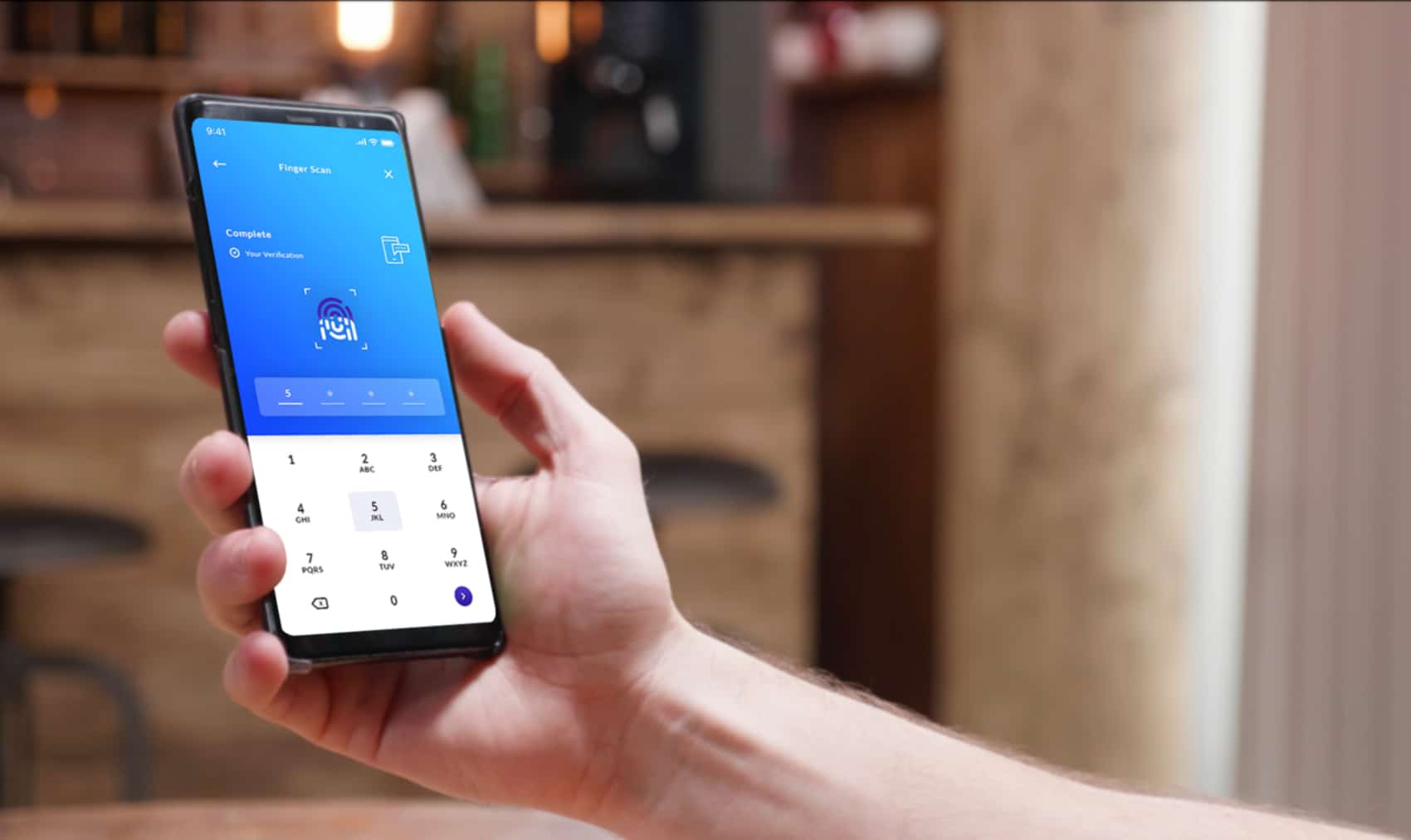
We use our mobile phones for almost everything. Beyond calls, chat and internet access, they have become our primary channel to pretty much every online service. Making payments is an obvious example, but increasingly accepting payment with smartphone mPOS apps (mobile point of sale) is important, as is applying for loans, obtaining and using travel tickets and a myriad of other use cases. Even auto makers are seeing the possibilities of using your phone as your car key – not just because it is already in your pocket – but because it enables new use cases such as car-sharing.
Trustonic’s Application Security solution is a toolkit that lets app writers develop applications that make use of the strongest security available – and on most Android smartphones that means the Trusted Execution Environment (TEE). An entire secure operating system running outside of the Android OS and protected by hardware within the CPU itself, the TEE is a surprisingly little-known feature, despite being present in almost all smartphones. The TEE is leveraged by all the key Android and OEM services – Keymaster, biometric unlock, Samsung Knox, Samsung Pay, and many others. Trustonic was at the forefront of TEE development from its inception, and our TEE implementation is the most prolific on the global market. Trustonic is also the only company to enable 3rd party application developers to leverage the full power of the TEE.
On many smartphones, this crucial but currently near-invisible secure subsystem has a rather amazing trick up its sleeve, which is about to make the TEE much more visible to everyday smartphone users.
Interact With the User via the Touch Screen in Isolation From the Main OS
When utilized correctly by app developers as part of an app’s UX, it can temporarily take over the screen and touch sensors of a smart device at the hardware level, giving what is called a Trusted User Interface (TUI). This is a UI feature in the developer’s toolbox that is particularly valuable during security-sensitive human interactions because malware in the main OS cannot attack it. The Android OS literally doesn’t have any access to the hardware during the period that the TUI is active – meaning that malware cannot capture the screen or simulate touches, even if the phone is rooted.
TUI is a great feature – but until now it has been impossibly hard to use. The low-level APIs provided are extremely low level – start, stop, blit image, detect touch. No widgets, no fonts, no text, no OpenGL. In practice, TUI was accessible to the very few expert developers, researchers and cybersecurity companies like Trustonic on the leading edge of new developments (we first wrote about TUI on this Blog in 2015).
With our latest version of Trustonic’s Application Security, we are very pleased to announce that that has all changed. TUI user interfaces can now be created using the new Layout Manager feature. This is a simple XML-based layout language, akin to Android layout, or HTML. A simple example:
For early access, please get in touch: enquiries@trustonic.com
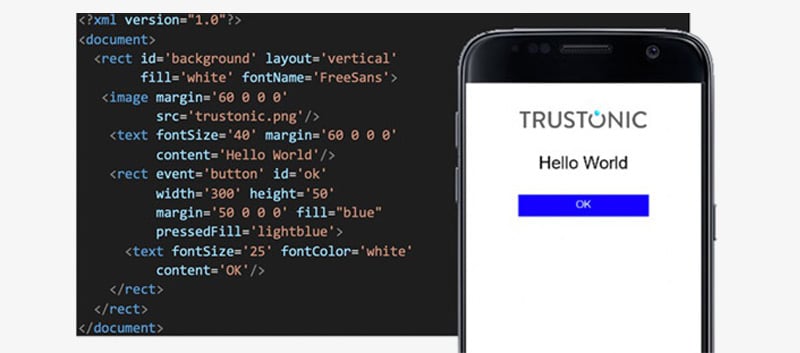
The Layout Manager XML language is simple and straightforward but belies a lot of power. There is full support for True Type and Open Type fonts (ensuring an attacker cannot mislead the user by replacing font assets), internationalization, buttons, menus, scrolling text and animation. As with a modern web browser, the UI is rendered as a Document Object Model (DOM) allowing application code to manipulate it as it sees fit – from simple examples such as pinpad, to full keyboards, scrolling text and images, to whatever else is needed.
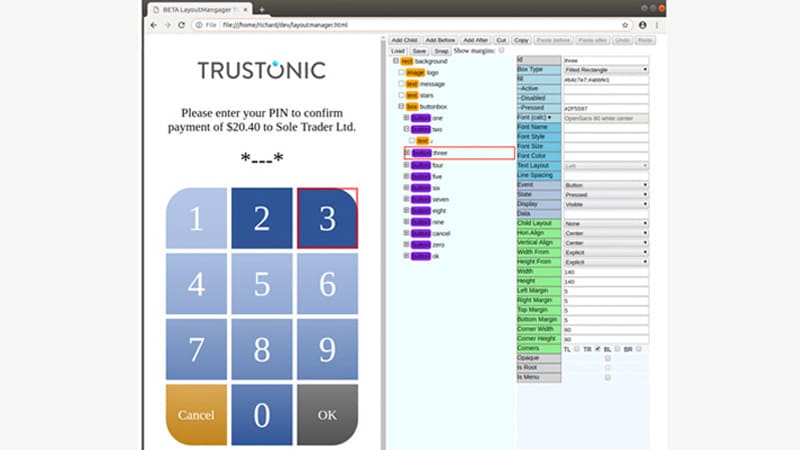
Whilst our Application Security solution provides all the necessary tools to product rich layout manager UIs defined in XML, we are also announcing today the beta availability of a graphical editor to create these UIs. This allows simple copy-paste editing and simulates the trusted UI directly in a web browser.
Layout Manger is backward compatible with all phones that shipped with the ‘low level’ TUI APIs – for example in the Samsung range, from the Samsung S6 onwards (Samsung was one of the first to use the technology as the company wanted TUI to better protect the Samsung Pay UI). This enables Trustonic’s Application Development partners to fully utilize TUI – and VW has lead the way, protecting their digital car key sharing using TAP and TUI, you can read about that here.
The past couple of years have seen a steady increase in understanding of TUI and its benefits, with forward-thinking developers in our dev community experimenting with TUI-protected interactions. The support for TUI is about to rapidly expand across more device makers and smartphone models and the wider app development community. With Android P the “Protected Confirmation” UI was introduced (a simple ‘secure confirm prompt’) and while this currently is not guaranteed to use TUI, that is very much the intent, and we can expect many more devices to support TUI in future.
https://android-developers.googleblog.com/2018/10/android-protected-confirmation.html
https://developer.android.com/training/articles/security-android-protected-confirmation
As with all new security features, TUI is not ubiquitous across all smartphones today – but Trustonic is committed to enabling the best security possible on every device. Our TAP platform includes a Software TEE, so that when a developer writes an app to leverage the power of the Hardware TEE, that app can also run on Android and iOS devices that do not provide access to the hardware protected secure TEE OS. Whilst Layout Manager is currently targeting only devices that support both a Hardware TEE and Hardware TUI, we will be adding support for all other classes of device in future releases.
We believe that protecting the most critical, sensitive, valuable (and hence most interesting to bad actors) interactions between users and their smartphone screens and keyboards is poised to shift rapidly towards the use of Trusted User Interface technology. This is why we are releasing our beta SDK to our developer community now.
Remember where you first read about the power of TUI!
For early access, please get in touch: enquiries@trustonic.com
Learn More
Discover our Cyber Security Platform for mobile, IoT and automotive. We also offer a Device Locking Platform for mobile operators, financiers and retailers.